The possibility of using a recalled password for login through RDP occurs when the Windows machine, which fits with Microsoft or Azure account, is set up to include access to the remote desktop. In this case, users can log in over RDP with a highly highlighted password, confirmed on locally stored accounting. In addition, users can be logged in using credentials for an online account that was used to log in.
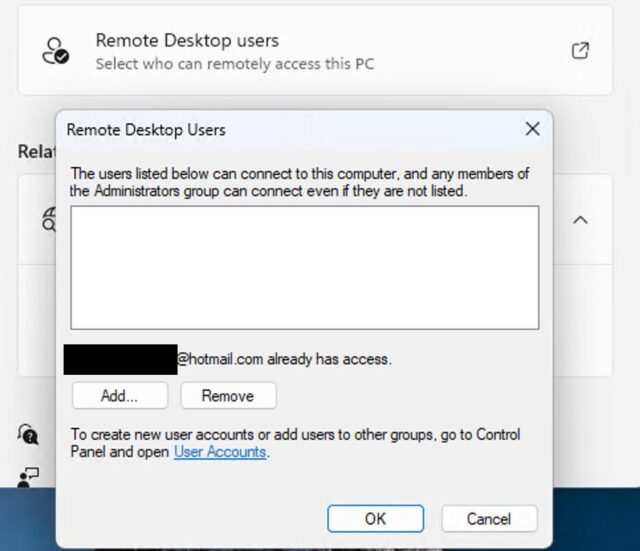
The screenshot of the RDP configuration window showing Microsoft account (for Hotmail) has remote access.
Even after users change their account password, but it remains valid to log in to RDP indefinitely. In some cases, Wade reports, some old passwords will work and the newer ones will not. Result: Sustainable access to RDP, which bypasses cloud -tested, multifactorial authentication and conditional access policy.
Wide and other Windows Security expert said little -known behavior may be expensive in scenarios when the Microsoft or Azure account has been violated, for example, when passwords are publicly seeped for them. In such an event, the first way of action is to change the password to prevent the enemy to use it to access sensitive resources. Although the password change prevents the enemy from entering the Microsoft or Azure account, the old password will provide an opponent of access to the user through RDP indefinitely.
“It creates a silent, distant rear in any system where the password has ever cachants,” Wide wrote in his report. “Even if the attacker never had access to this system, Windows will still trust the password.”
Villa Dormann, a senior analyst of vulnerability in the field of Analygence, agreed.
“It makes no sense in terms of security,” he wrote in an interview on the Internet. “If I am Sizadmin, I would expect that at the moment I change the account password, then the old credential credentials of this account cannot be used anywhere. But this is not so.”
Capting trust is a problem
The mechanism that makes it all possible is cacheting of the credentials on the hard drive of the local machine. The first time the user is included in the use of Microsoft or Azure credentials, RDP will confirm the password’s validity on the Internet. Then Windows saves an account in cryptographically protected format on a local machine. Since then, Windows has confirmed any password entered when you sign in to RDP, comparing it with a locally stored account, without searching on the Internet. With this, the withdrawal password will still provide remote access through RDP.
Source link
Biz & IT,Security,passwords,Remote Desktop Protocol,Windows , , #Windows #RDP #log #recalled #passwords #Microsoft, #Windows #RDP #log #recalled #passwords #Microsoft, 1746040087, windows-rdp-allows-you-to-log-in-with-the-recalled-passwords-microsoft-with-this-ok
